Introduction and Context:
Human nature tends to be reactive, and the traditional IT operations response mode has been to wait for something to break and then act. The adage “if it isn't broken, why fix it?” where incidents are often addressed after they occur has become unconventional and unwise. Consequently, in today’s hyper-connected services and data sharing environments, taking a wait and see approach has particular risks for companies proprietary data, trade secrets, personal identifiable information (PII) and intellectual property (IP). Traditional reactive modes are no longer sufficient, as they often lead to financial loss, investigation, reputational damage, and regulatory non-compliance. The security threat landscape is evolving to include malware-free attacks, up 71% in 2022, and Vishing involving human actors, and other more sophisticated techniques (Learn more: The State of Security 2023 (splunk.com), CrowdStrike2023GlobalThreatReport.pdf)
A boutique financial technology services (fintech) company successfully implemented a Security Information and Event Management (SIEM) solution to mitigate threats and raise customer confidence in data security, and ultimately safeguarding their business while enhancing operational efficiency.
Problem:
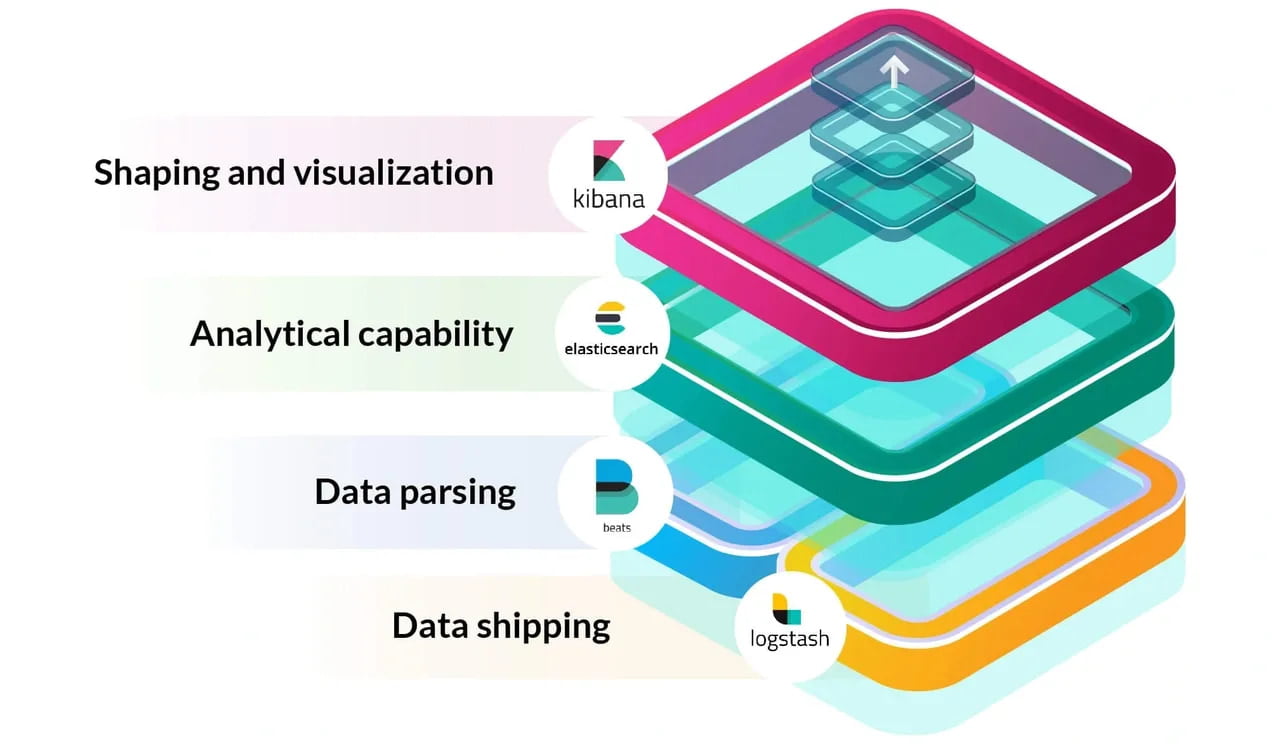
Ingenium Grex Solution:
Capabilities enabled:
- Threat Detection and Prevention: Real-time monitoring and analysis of security events, facilitating the detection and prevention of cyber threats. It helps identify unauthorized access attempts, malware infections, data breaches, insider threats, and more.
- Centralized Log Management: Consolidates logs and security event data from all infrastructure devices, providing efficient analysis, correlation, and reporting capabilities; together enabling pattern matching, weaknesses, and anomalies.
- Compliance and Regulatory Requirements: Helps meet stringent regulatory frameworks – SOC2 Type II, PCI DSS and GDPR.
- Incident Response and Forensics: Quick investigation, root cause analysis, tracking of attack vectors, and gathering of evidence for remediation and potential legal proceedings.
- Insider Threat Detection: Detect suspicious activities by employees or privileged users, providing early warnings about potential insider threats.
- Operational Efficiency: With automation and advanced analytics capabilities, end-user struggles, such as multiple PW attempts, are identified in the log data, surfaced, and the user is proactively contacted.
Lessons:
- Prioritize Compliance: Compliance requirements are a significant driver in executive decision making about improving the company's security posture, ensuring adherence to regulatory frameworks and industry standards for security integrity. This will increasingly be a baseline requirement for all companies.
- Invest Time in Tuning: Tuning the SIEM system to focus on impactful and critical log events is crucial. With a vast number of events, fine-tuning helps surface actionable data and reduces noise.
- Align with Business Goals: Collaborate with business leaders to identify baseline requirements, what’s important and what could be deprioritized, to ensure the available resources (including human capital) are efficiently used and aligned with availability and performance objectives of the IT infrastructure.
Jai Ragoo is a Senior Security Architect with deep experience in proactive posture management, threat analysis, operations incident response and efficiency, and their supporting infrastructure services. He is a Senior Advisory Consultant to Ingenium Grex. He can be reached at progress@ingrex.net.

